Phishing

Phishing is a type of online scam where attackers impersonate legitimate organizations or individuals to trick people into providing sensitive information, such as passwords, credit card numbers, or personal details. They often use deceptive emails, messages, or websites to carry out the scam.
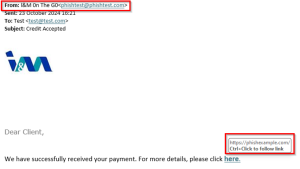
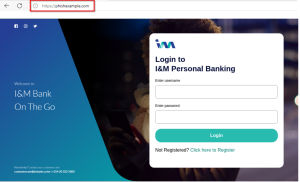
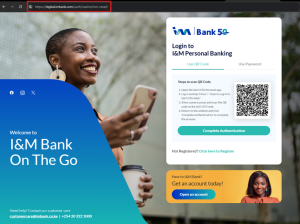
Example:

Fake site Legitimate I&M Site


Can you spot the differences/ red flags?
- All I&M communications originate from the email address information@imbank.co.ke or onthego@imbank.co.ke.
- All I&M Bank internet banking webpages contain the domain: digital.imbank.com ie Retail Customers login: https://digital.imbank.com/inm-retail/login , Corporate customers login: https://digital.imbank.com/inm-corporate/login
- Any concerns or queries can be reported to: customercare@imbank.co.ke or call 0719 088 000,0732 100 000 . We operate 24/7 to ensure your safety and service.